SANS Institute on Twitter: "We're counting down the #20CoolestCareers in #Cybersecurity #SSA #15 -#SecurityAwareness Officer (retweet if this is your job role) Want to identify top human risks and the behaviors in

SANS Top 25 Most Dangerous Programming Errors Catagory 1: Insecure Interaction Between Components These weaknesses are related to insecure ways. - ppt download

System Defense Defending Home Networks. Introduction Computer Security What it's not Person, Place or Thing What it is Independent –Of Network OS –Of. - ppt download
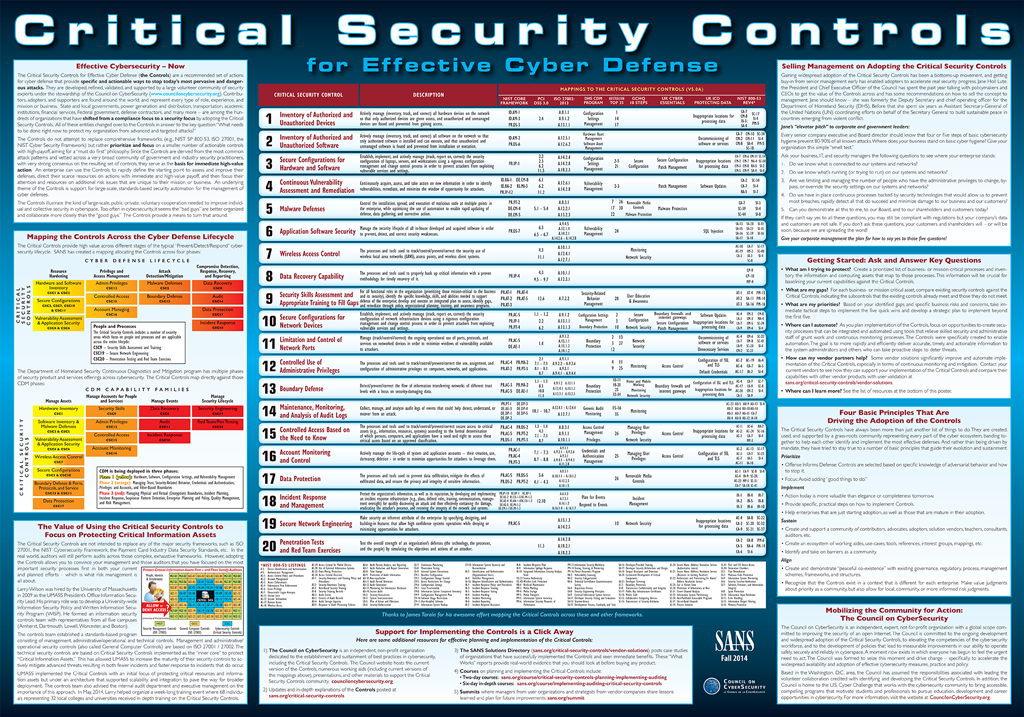
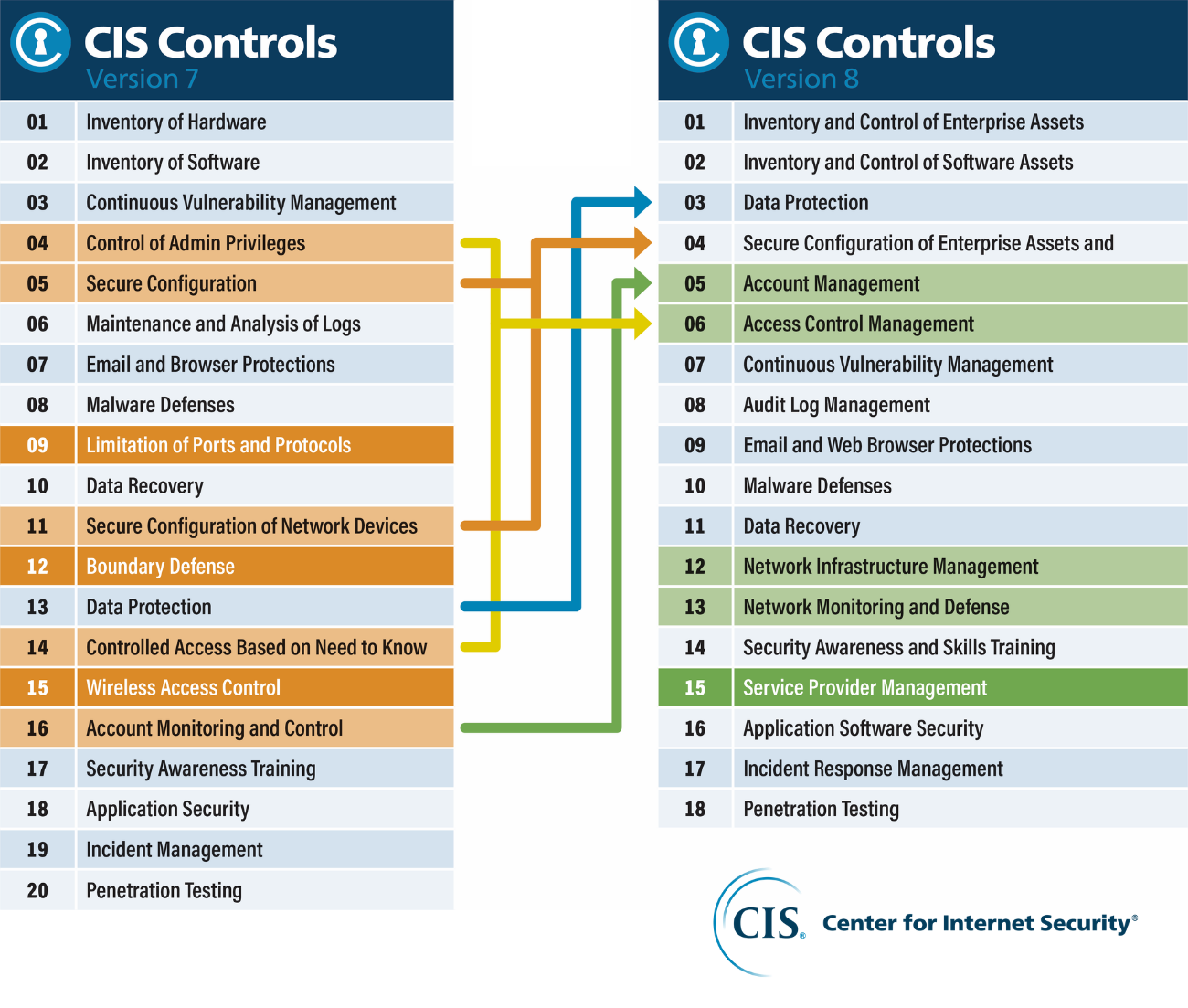
SANS Institute on X: "20 CRITICAL SECURITY CONTROLS | POSTER: Set of actions for cyber defense. DL > PDF (2pgs) - http://t.co/YZGlCbuXmd http://t.co/moeIozrqu0" / X